In our increasingly digital world, where most of our activities involve the use of computers and the internet, security has become more vital than before. Due to the increased cases of working from home and the use of the internet to conduct various tasks safety of our data and privacy is very important. A Virtual Private Network also known as VPN is one of many tools that individuals widely apply to increase their level of security while using the internet.
If you want to learn more about VPNs like what are these and how they work you must visit our guide. In the following article under discussion, the reader will find information about the use of VPNs in internet security, how they function, advantages and disadvantages, and cautionary measures for safer browsing.
VPN further becomes important in internet security as the world shifts to the digital world further. VPNs assist in developing a protected and personal link to the internet to browse securely and view the contents that can be blocked. However, the utilization of VPNs also has certain drawbacks regardless of the benefits it presents. It is crucial to understand such risks if one wants to improve their security on the World Wide Web.
Understanding VPN Security Risks
Where VPNs Can Get in Trouble
VPNs are such networks that encrypt your connection so that your activities on the Internet cannot be tracked. Yet, they may also serve as the weak spots that hackers and other malicious actors can exploit. When a VPN is not well configured or if the VPN contains certain vulnerabilities, such hackers can always take advantage of the weaknesses. For instance, when a VPN provider does not frequently update the software used to create the VPN connections, then the VPN connections become vulnerable to attacks that may lead to leakage of information that belongs to the users of the VPNs.
Exploiting VPN Protocols
VPNs use various protocols to initiate and set up a connection as well as for the creation of a secure connection. Certain protocols of serial communications, which are employed in some of these applications are however known to have these frailties. For instance, the early VPN protocols hold relatively lesser security than the present ones like OpenVPN/ IKEv2. Such vulnerabilities can be exploited by hackers in such a way that enables them to receive the data or sneak into a particular network.
Rise in VPN Exploits
As to the new form of working from home, cases of misuse of VPNs are prevalent most of the time. No one can argue with the fact, that hackers have targeted those organizations that rely purely on VPNs to establish remote access. It has been highlighted within recent months that companies are bearing the impact of attacks that exploit the weaknesses within the VPN and lead to data breaches and ransomware attacks.
Top VPN-Related Threats
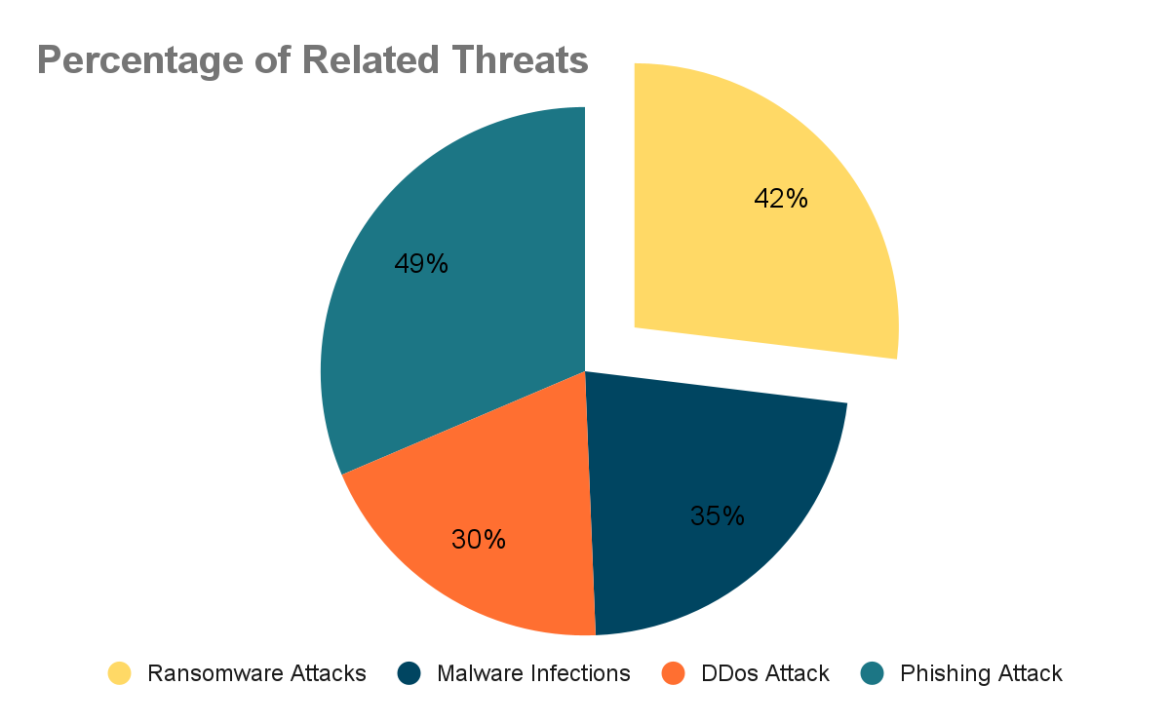
Still, it is vital to understand the threats that are related to VPN usage as it is profitable for all participants. Here are some of the most common VPN-related threats:
Ransomware Attacks (42%)
Ransomware could be referred to as a category of malware that locks files on a user’s computer and then demands to be paid to unlock the files. VPNs are at risk of ransomware attacks for the purpose of disrupting of the organization and the attainment of the attackers’ objectives, namely the interception of valuable information. After gaining access to a network, they can increase the ransomware’s coverage to other connected gadgets, which results in massive data leakage and financial repercussions.
Malware Infections (35%)
Malware can enter devices that connect to a VPN. Thus, if a user downloads unverified files unintentionally while connected to a VPN, the malicious files will spread all over the VPN. This is more worrying for business organizations because one device can harbor the virus that affects all the others.
DDoS Attacks (30%)
Distributed Denial of Service is a type of attack where many systems send traffic to a targeted system so that the targeted system becomes overloaded and crashes. Attackers can also hide behind VPN and this makes it very hard for security personnel to track the source of the attack. This situation may result in long closures of business ventures and consequently, loss of revenues.
Phishing Attacks (49%)
Phishing is a type of attack that is based on deceiving the users and making them divulge personal information like passwords or credit card numbers. Again VPN does not act as a shield against these scams, and one can easily fall prey to such scams. Phishing emails are commonly used by hackers to bypass weaknesses in organizational security by acquiring users’ VPN login information.
If you’re still interested and want to dive deeper into these data threats, be sure to check out our comprehensive guide. We’re confident you’ll find it valuable.
The Limitations of Traditional VPNs
VPNs work and include an extra layer of protection; however, their disadvantages can put users in harm’s way. Here are some of the main drawbacks of traditional VPNs: are
Inability to Contain Lateral Movement
When a malicious user penetrates into a network using a VPN, the latter can explore other devices within the network and gather additional information. Lateral movement is not confined by traditional VPNs and thus allows attackers to spread malware and steal information.
Reliance on Outdated Infrastructure
Moreover, it is still a fact that the majority of organizations use rather limited and outdated VPN infrastructure, and it is quite probable that it is not secure enough. They become extremely vulnerable if these systems are not regularly updated with correlative patches. In most of the areas mentioned above, it is clear that such scenarios delight cybercriminals due to the possibilities they offer them.
Security Threats Mitigated by Internet Confronting VPN Appliances
Worse still, the connected network VPN appliances that interface with the Internet can become the main target of the adversaries. If the VPN is not properly configured, it means that there are other users from the outside with direct access to the actual network. This stresses the need for the proper and secure settings of VPN systems together with their constant monitoring.
Moving towards the Zero Trust Model
Therefore, owing to the difficulties attributed to traditional VPNs, many corporations are turning to the zero-trust security model. It lowers the opened ports and the vulnerable points of the profile by tightening down on the security measures. Here’s how the Zero Trust model enhances internet security:
Embracing Zero Trust Architecture
Zero trust positioning uses the type of thinking, that presupposes that threats can come from both inside and outside the network. Thus, it includes user identities associated with these resources as well as the devices used to access the information go through constant verification. In other words, the more organizations implement the Zero Trust approach, the extent of threat regarding the VPN connections is reduced and, therefore, increases protection for restricted data.
Eliminating Legacy Technologies
The Zero Trust model for example urges organizations not to rely on what it terms as traditional solutions like the VPN or the firewall. Thus, it can be stated that it is more specific and is related to identity-based access at the application level rather than the network level. This means that permission is granted on the grounds of identity as well as the security features of the gadgets used and not the VPN.
Implementing Zero Trust Strategies
To adopt a zero-trust approach, organizations should implement strategies such as:
- Micro-segmentation: They provide segmentation of the network into various sub-sections in order to prevent unauthorized personnel from accessing and instances of leakage.
- Continuous monitoring: Continuously scanning the users and the devices of the organization to identify signs of abnormal behavior.
- Strict access controls: Implementing the regulation of documents accessible in an organization via roles and privileges of the users.
Secure Remote Access Solution Guide
To enhance the role of VPNs in internet security, users and organizations should follow best practices for secure remote access:
1. Automate Security Updates
It is necessary to update the VPN software frequently to prevent and avoid such shortages. Security updates can be set to go automatically, this will ensure that the users are always protected by the latest update.
2. Support Device Authentication
Based on the above points, the following measures can be stated: Device authentication allows one to be sure that only allowed devices are able to connect to the VPN. This provides one more level of security so that no unauthorized personnel would be granted access.
3. Enforce Multi-Factor Authentication (MFA)
MFA as implemented by Voom to secure its VPN means that VPN users must authenticate themselves two or more times. This lowers the probability to a great extent of passwords and subsequently the possibility of gaining entry by an unauthorized person.
4. Session Recordings and Logs
Information on user sessions and logs can assist in identifying the suspicious activity of users. The above information can be useful in the audit and optimization of security processes.
5. Offer Endpoint Security Solutions
Utilizing two endpoint security measures can enhance the security of the devices connecting to the company VPN against various threats such as malware. These are general protection tools such as antivirus and firewall systems and intrusion detection systems.
Frequently Asked Questions (FAQs)
Are VPNs safe enough for personal use?
VPNs are in majority safe and enhance your security online. These cover your location and your data is encrypted. However, it concerns selecting a credible VPN service to cooperate with. Note that there are some VPNs that can be used for free and among them can be some crooks who can sell your data.
In what ways does a VPN work to protect you while using the internet?
Remember that a VPN establishes a secure channel through which your Internet connection will go through. It conceals your actual position and also encodes your information. This makes it difficult for hackers to steal your information. That would also assist in escaping the geographic limitations of certain pieces of content.
Why are VPNs more effective than other solutions for protection of your data and anonymity online?
In comparison with the other techniques, VPN presents a full security level more efficiently. They mask your location, secure all your internet connections, and operate on all your applications. They also allow users to unblock restricted geographical content and safeguard them on unsecured Wi-Fi connections.
Are VPNs useful to Hide Your Data When You are Browsing Online?
Yes, that is correct VPN is very effective in maintaining our privacy as well as our safety while using the internet. They protect your natural IP address and encode your information. This makes it hard for others to pursue you or to follow your info, it also makes it very difficult for anyone to unjustly extract your information. But of course, no security method is foolproof.
What are the steps I should take to make my connection safer and more private using a VPN?
First depends on selecting a good VPN service. Get their application installed on your device. Go to the website and sign up to create a username and password. Select the server location and log into it. It is recommended to turn on the VPN before browsing the internet. To confirm whether it’s working; you can try entering “What’s my IP?”
Is VyprVPN safe to use to maintain anonymity while browsing the internet?
All in all, VyprVPN is relatively dependable for improving the first and the second layers of internet privacy and security. No IP logs are kept, the provider is using its own server, and the privacy policy does not allow downloading logs to third parties. However, always compare different VPNs and make sure to read the latest reviews before making that final decision.
Conclusion
This article provides a comprehensive analysis of how VPNs function with the positioning of safeguarding internet security as crucial in the present day. Although VPNs act as the shield of the troopers, they are not impervious. The information provided in the paper shows that it is possible to improve security measures by knowing the threats concerning VPNs and applying the zero-trust model approach. Thus, users and organizations are able to maintain the highest levels of protection with the help of adherence to the best practices and being aware of the recent threats.
While further exploring the threats that are inherent in the context of internet security it is of crucial importance to address the shifting purposes of VPNs. They can however be very effective in this fight if used correctly and supplemented with other security solutions. Therefore, a safer approach to social media platforms is achievable if security measures are enhanced to check on people’s ill-perceived behaviors.


